windows蓝屏分析BSOD-ExpScanGeneralLookasideList引用ffffffffffffffd8地址IRQL_NOT_LESS_OR_EQUAL
本文的完成得到了QQ windows驱动开发交流群(938840300)群主的帮助,感谢他的原始分析。这里本人基于它的原始分析在第二次蓝屏DMP上按照它的思路完成该文。
同事说最近出一个蓝屏,让分析一下。使用Windbg加载信息如下:
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: ffffffffffffffd8, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80265dbd320, address which referenced memory
典型的内存错误,本想着一个比较容易定位的问题,没想到还是有些不容易的。
首先就是这个地此用的地址是ffffffffffffffd8,是这个一明显有问题的地址。平时引用的地址要么是“NULL”地址,要么是有意义的地址,看来这个地址上来就给了一个下马威。
再看一下trap frame
PROCESS_NAME: System
TRAP_FRAME: ffffb80cf4f0a2a0 -- (.trap 0xffffb80cf4f0a2a0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000000 rbx=0000000000000000 rcx=0000000000000000
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80265dbd320 rsp=ffffb80cf4f0a430 rbp=000000000000ffff
r8=0000000000000000 r9=0000000000000004 r10=0000000000000000
r11=0000000000000100 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na po cy
nt!ExpScanGeneralLookasideList+0x40:
fffff802`65dbd320 418b48d8 mov ecx,dword ptr [r8-28h] ds:ffffffff`ffffffd8=????????
Resetting default scope
再看一下栈回溯。
2: kd> k
# Child-SP RetAddr Call Site
00 ffffb80c`f4f0a158 fffff802`65e7fbe9 nt!KeBugCheckEx
01 ffffb80c`f4f0a160 fffff802`65e7bfd4 nt!KiBugCheckDispatch+0x69
02 ffffb80c`f4f0a2a0 fffff802`65dbd320 nt!KiPageFault+0x454
03 ffffb80c`f4f0a430 fffff802`65e3aead nt!ExpScanGeneralLookasideList+0x40
04 ffffb80c`f4f0a460 fffff802`65de2df5 nt!KeBalanceSetManager+0x10d
05 ffffb80c`f4f0a550 fffff802`65e7579c nt!PspSystemThreadStartup+0x55
06 ffffb80c`f4f0a5a0 00000000`00000000 nt!KiStartSystemThread+0x1c
呃,挂在了内核中,可以看到是由于ExpScanGeneralLookasideList函数引起的。而这个函数的调用是内存负载均衡线程KeBalanceSetManager在扫描非分页快查表发生了缺页导致蓝屏。
我们分析一下上面的trap fame
2: kd> .trap 0xffffb80cf4f0a2a0
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000000 rbx=0000000000000000 rcx=0000000000000000
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80265dbd320 rsp=ffffb80cf4f0a430 rbp=000000000000ffff
r8=0000000000000000 r9=0000000000000004 r10=0000000000000000
r11=0000000000000100 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na po cy
nt!ExpScanGeneralLookasideList+0x40:
fffff802`65dbd320 418b48d8 mov ecx,dword ptr [r8-28h] ds:ffffffff`ffffffd8=????????
而当前的 r8=0000000000000000 ,明显看到是一个NULL地址。
我们反汇编一下ExpScanGeneralLookasideList函数。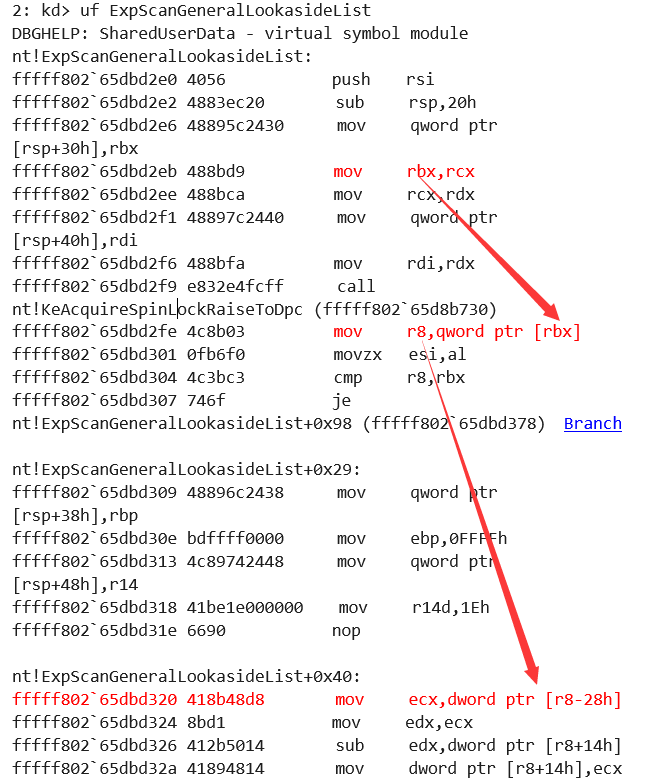
可以看到rbx最终来源于RCX,而rcx我们通过x64反汇编可知,其实是该函数的第一个参数。当然Windows驱动开发源的群主也用IDA做了很详尽的分析,其原内容如下:
寄存器r8显然是个无效内存,我们通过ida分析一下数据的来源
如下所示函数ExpScanGeneralLookasideList参数,分别为
- 第一个参数:ExNPagedLookasideListHead
- 第二个参数:ExNPagedLookasideLock
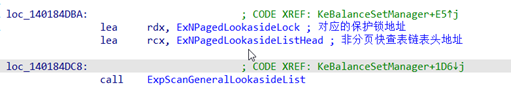
可见是遍历ExNPagedLookasideListHead链表过程中,发现链表节点有损坏导致蓝屏的,现在windbg手动遍历一下
2: kd> !list ExNPagedLookasideListHead
fffff802`660b9f70 fffff802`660eda00 ffffa785`9d516a20
fffff802`660b9f80 00000000`00000000 00000000`00000000
fffff802`660b9f90 fffff802`660b9f90 fffff802`660b9f90
fffff802`660b9fa0 00000000`00000000 00000000`00000000
fffff802`660b9fb0 fffff802`660bcc40 ffffa785`911d25c0
fffff802`660b9fc0 00000000`00001001 ffffbbc7`00003000
fffff802`660b9fd0 00000000`00000000 00000000`0000007f
fffff802`660b9fe0 00000000`00000080 ffffa785`89010000
fffff802`660eda00 fffff802`6618dd80 fffff802`660b9f70
fffff802`660eda10 00000000`00000000 00000000`00000000
fffff802`660eda20 00000000`00000000 00000000`00000000
fffff802`660eda30 00000000`00000000 00000000`00000000
fffff802`660eda40 00000000`00000000 00000000`00000000
fffff802`660eda50 00000000`00000000 00000000`00000000
fffff802`660eda60 00000000`00000000 ffff9e00`0000b0d8
fffff802`660eda70 ffff9e00`0000b168 00000000`00027fe0
....太多了,省略掉了....
ffffa785`9d3b1e10 ffffa785`9df09220 ffffa785`9be362d0
ffffa785`9d3b1e20 00000000`00000000 00000000`00000000
ffffa785`9d3b1e30 00000000`00000000 00000000`00000000
ffffa785`9d3b1e40 00000000`00000000 00000000`00000000
ffffa785`9d3b1e50 00000000`00000000 00000000`00000000
ffffa785`9d3b1e60 fffff802`6fa8c5b0 ffffa785`9d3b1b50
ffffa785`9d3b1e70 ffffa785`975de090 00000000`00000000
ffffa785`9d3b1e80 ffffa785`9d3b1e80 ffffa785`9d3b1e80
ffffa785`9df09220 ffffa785`9d5169a0 ffffa785`9d3b1e10
ffffa785`9df09230 00000000`00000000 00000000`00000000
ffffa785`9df09240 00000000`00000000 00000000`00000000
ffffa785`9df09250 00000000`00000000 00000000`00000000
ffffa785`9df09260 00000000`000001b0 00000000`00000000
ffffa785`9df09270 00000000`00000000 00000000`00000000
ffffa785`9df09280 00000000`00000000 00000000`00000000
ffffa785`9df09290 00000000`00000000 00000000`00000000
ffffa785`9d5169a0 00000000`00000000 00000000`00000000
ffffa785`9d5169b0 00000000`00000000 00000000`00000000
ffffa785`9d5169c0 00000000`00000000 00000000`00000000
ffffa785`9d5169d0 00000000`00000000 00000000`00000000
ffffa785`9d5169e0 00000000`00000000 00000000`00000000
ffffa785`9d5169f0 00000000`00000000 00000000`00000000
ffffa785`9d516a00 00000000`00000000 ffffa785`9c727060
ffffa785`9d516a10 00000000`00000000 00000000`00000000
我们回过来头再看,空地址0-0x28=0xFFFFFFFFFFFFFFD8完美地对应上了windbg分析上的错误
 Windows蓝屏分析
Windows蓝屏分析





